How Does Extensible Authentication Protocol Work
Extensible Authentication Protocol Transport Layer Security EAP-TLS is an IETF open standard thats defined in RFC 5216. It conveys identity data between an identity provider IdP and a service provider SP.

Authentication For Dummies Eap Peap Leap Youtube
The authenticator which grants access.
. The EAP protocol can support multiple authentication mechanisms without having. Each one works differently but they all do the same thing. Protected Extensible Authentication Protocol PEAP is an 8021X authentication type for wireless LANs WLANs.
Extensible Authentication Protocol EAP is an authentication framework not a specific authentication mechanism frequently used in wireless networks and point-to-point connections. And the authentication server which gives permission. Its major scope is wireless network communication such as access points used to authenticate client.
How does Passwordless EAPExtensible Authentication Protocol operate. The Extensible Authentication Protocol EAP is a protocol for wireless networks that expands the authentication methods used by the Point-to-Point Protocol a protocol often used when connecting a computer to the internet. As you say there are a variety of EAP protocols.
Protected Extensible Authentication Protocol PEAP PEAP like all other EAP methods determines how authentication materials are protected. For example an administrator who requires digital certificate-based authentication might deploy the EAP-TLS method. Extensible Authentication Protocol is an authentication resource for wireless networks and point-to-point setups.
What I know. The authentication server asks the access point for proof of the validity of the ID. 8021X is the standard that is used for passing EAP over wired and wireless Local Area Networks LAN.
I have searched but cant find an answer that makes sense to me. Im purposely using the word Materials as there is nothing saying the authentication mechanism has to be a usernamepassword. You could call EAP a protocol or you could call it a framework of protocols where each variant like EAP-FAST is a protocol.
One of these is Extensible Authentication Protocol Transport Layer Security EAP-TLS a protocol that is popular for local area networks. The supplicant is needed because it initiates the connection by engaging in an Extensible Authentication Protocol EAP transaction between the supplicant and the controller or switch. When a user wants to access a wireless network the access point requests authentication information from the user and the received response is sent to the authentication server.
As a general framework this protocol is useful in many different variations. PEAP provides a transport layer security structure where it is. SAML is an open authentication standard based on extensible mark-up language XML.
The authentication server asks the access point for proof of the validity of the ID. How does Passwordless EAPExtensible Authentication Protocol operate. EAP methods operate within the EAP framework to support a variety of authentication techniques.
The supplicant has an identity and some credentials to prove that it is who it claims to be. This protocol is used to create a simple link between two peers in a network to transport packetsPPP links are full-duplex and deliver packets in order. The Extensible Authentication Protocol EAP enables extensible authentication for network access.
The supplicant gathers the credentials of the user together in a way that corresponds with what 8021X can read. EAP is used to authenticate simple dialup and LAN connections. Point-to-Point Protocol or PPP is a layer 2 or data link layer protocol that is used to establish a direct connection between two nodes in a network.
Extensible Authentication Protocol EAP is an authentication framework that is used to authenticate dial-up or VPN connections. Extensible Authentication Protocol EAP is a point-to-point P2P wireless and local area network LAN data communication framework providing a variety of authentication mechanisms. EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods.
For more information see. The Extensible Authentication Protocol EAP is a protocol for wireless networks that expands on authentication methods used by the Point-to-Point Protocol PPP a protocol often used when connecting a computer to the Internet. The standard authentication protocol used on encrypted networks is Extensible Authentication Protocol EAP which provides a secure method to send identifying information over-the-air for network authentication.
The name implies that its a protocol Question. How exactly does Extensible Authentication Protocol EAPProtected EAP integrate into modern security protocols. EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication.
The authentication is based on a three-party model. EAP-TLS is considered the gold standard for network. It provides some common functions and negotiation of authentication methods called EAP methods.
It can provide authentication encryption and compression. LEAP PEAP EAP-FAST EAP-TLS etc. The Extensible Authentication Protocol EAP is a protocol for wireless networks that expands on authentication methods used by the Point-to-Point Protocol PPP a protocol often used when connecting a computer to the Internet.
PEAP provides strong security user database extensibility and support for one-time token authentication and password change or aging. Extensible Authentication Protocol EAP is an authentication framework frequently used in network and internet connectionsIt is defined in RFC 3748 which made RFC 2284 obsolete and is updated by RFC 5247. Click to see full answer.
Authenticate a user before allowing them access to a wireless network. The supplicant which requires access. Its used by wireless networks utilizing authentication methods based upon Point to Point Protocol PPP.
Extensible Authentication Protocol EAP can be. More colloquially EAP-TLS is the authentication protocol most commonly deployed on WPA2-Enterprise networks to enable the use of X509 digital certificates for authentication. In this case the IdP authenticates the identity and passes the information in an XML format to an SP which authorizes the given identity to access the requested services.
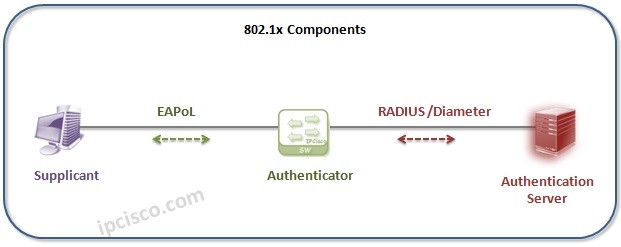
Eapol 802 1x Extensible Authentication Protocol Over Lan Ipcisco

Figure 4 From Extensible Authentication Protocol Eap And Ieee 802 1x Tutorial And Empirical Experience Semantic Scholar

802 1x Extensible Authentication Protocol Flexible Authentication Via Secure Tunnelling
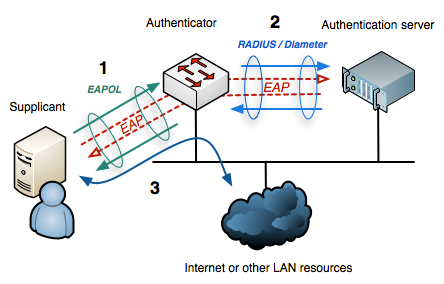
What Is 802 1x Authentication And How It Works Study Ccna
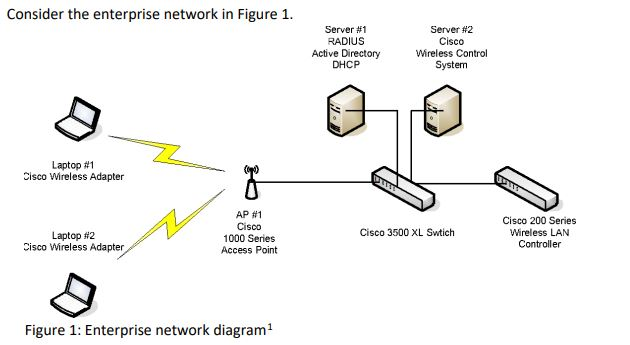
Solved Discuss The Use Of Extensible Authentication Protocol Chegg Com
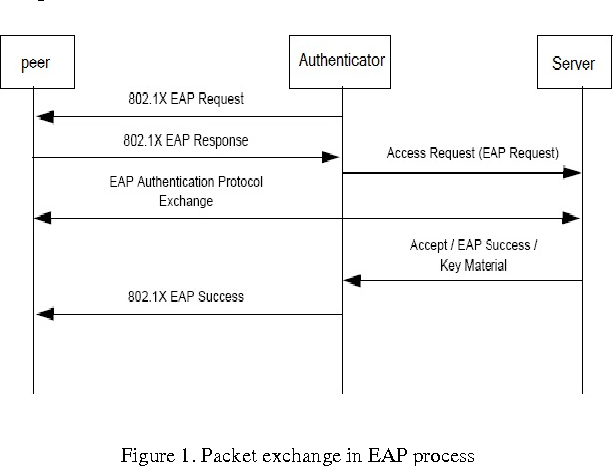
Figure 1 From Implementation Of Extensible Authentication Protocol In Opnet Modeller Semantic Scholar

Eap Faka Authentication Protocol Download Scientific Diagram
802 1x And Eap Authentication Protocols

802 1x Eap Authentication Protocols Ppt Video Online Download

3 Introduction To Extensible Authentication Protocol Eap Youtube

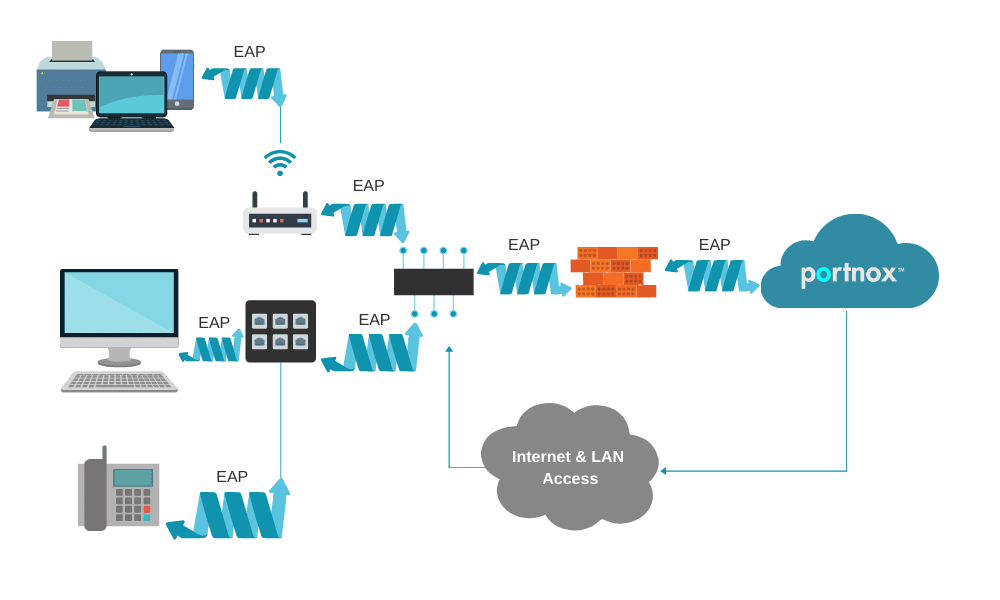
802 1x Protocol For Network Authentication Portnox

Authentication Protocol 802 Dot 1x And Eap Types For Wired And Wireless Authentication Learn Solve It
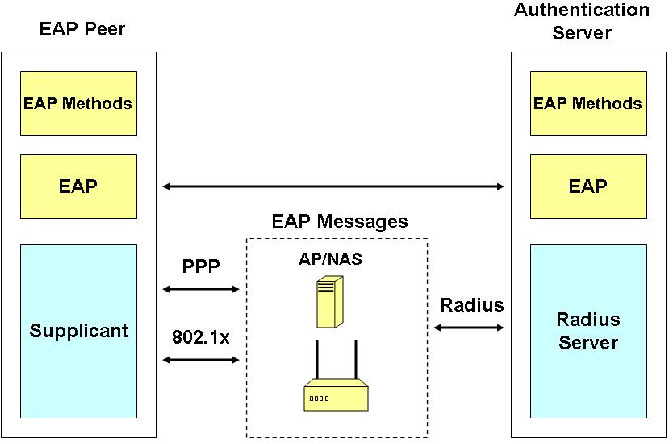
Pdf Extensible Authentication Protocol Eap Security Issues Semantic Scholar
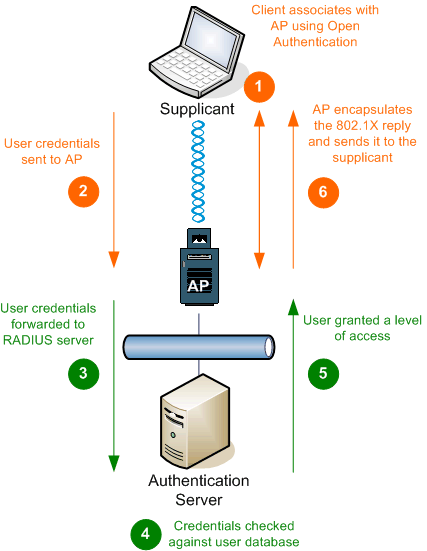
802 1x Extensible Authentication Protocol Flexible Authentication Via Secure Tunnelling

Ms Peap Overview Microsoft Docs

Extensible Authentication Protocol Eap Pass Through Model Download Scientific Diagram
What Does Extensive Security Protocols Mean Quora
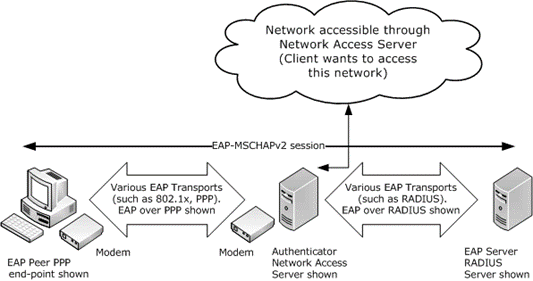
Ms Chap Overview Microsoft Docs

What Is Extensible Authentication Protocol Eap And How Does It Work The Security Buddy

Comments
Post a Comment